If you need to get information on a host that has been scanning your perimeter, try SNIPEHUNT!
Automate admin tasks and hacking (maintaining access) with graSSHopper!
I made this little tool to automate some administrative tasks such as finding uptime and patch status, but it can be used for much more. Give it a try and feel free to contribute: https://github.com/b3b0/graSSHopper
RELEASES
VERSION 1.1
It’s recommended that you remove previous versions of graSSHopper before installing the latest
PURPOSE
To automate administative tasks, operational auditing, and hacking.
DEPENDENCIES
- Unix-based OS
- Ruby
- Python
- SSH client
- sudo
INSTRUCTIONS
- If using source,
cd graSSHopper-master - Also if using source,
sudo bash install.sh - Configure your
/usr/share/grasshopper/commands.cfgand/usr/share/grasshopper/servers.cfgfiles appropriately withgrasshopper -candgrasshopper -s
EXAMPLE COMMANDS.CFG FILE
df -h && uptime
EXAMPLE SERVERS.CFG FILE
10.0.0.254, john, 22 myawesomeserver, admin, 22
- Run the program with
grasshopperor usegrasshopper -afor crontab. - Get extra help with
grasshopper -horman grasshopper - Run through the ssh-keygen setup
- You’re golden ponyboy
USAGE
$ grasshopper -h
GRASSHOPPER
NAME
grasshopper - run commands against multiple servers.
SYNOPSIS
grasshopper [OPTION]
DESCRIPTION
Run commands against multiple serves with user input or as a crontab job.
USAGE:
- h: Display this menu
- a: automatic, runs commands in commands.cfg against servers in servers.cfg
- c: Edit commands.cfg
- s: Edit servers.cfg
OTHER
- Plan to add quick way to edit commands.cfg and servers.cfg within the program.
- Contribute, break, fix or shame the project. It’s cool man.
LICENSE
---graSSHopper---
(https://github.com/b3b0/graSSHopper)
Copyright (C) 2018 Dustin Davis (b3b0)
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
Automate the drudgery with nventory!
https://github.com/b3b0/nventory
nventory
A light-weight NMAP wrapper based on https://github.com/argp/nmapdb.

Dependencies:
- Linux, MacOSX
- python2
- libsqlite3-dev
- pysqlite (https://pypi.python.org/pypi/pysqlite)
Installation:
- cd to
$ nventory-master/installer $ sudo python2 install.py- You’re done!
Usage:
$ nventory
What’s next?
Everything else from this point is straight-forward.
You can use list files (-iL) for inventorying multiple hosts.
You can explicitly type specifc single hosts for inventory as well.
All working elements of this software are located at /opt/nventory.
Actual database location: /opt/nventory/database/database.db.
Feel free to fork it / break it / bop it.
-b3b0🐧💻🔑
Use SCCM 2012 Configuration Baselines to find Spectre / Meltdown Vulnerabilities with GameBoyHorror!

This will be a very brief post, as there is not much to explain.
SCCM 2012 administrators should know how to create configuration items and baselines, so simply plug in the code from my fork of burntmacncheese’s project and make sure you set compliance settings to look for “Success.” as the output of the script, any other result being non-compliant.
This version ONLY checks to see if a workstation or server has applied 2018-01-09 updates to mitigate the vulnerability risk at the OS level. Feel free to fork / bork it to check for full mitigation at the hardware level.
https://github.com/b3b0/GameBoyHorror
Have fun specter hunting!
-b3b0🐧💻🔑
How to survive a trip abroad with no cellular service or data

Plan on taking a trip to another country? Don’t feel like fighting with international roaming fees while being able to navigate, translate and keep in touch with your loved ones?
Stick around – I have some advice for you.
My girlfriend and I just got home from a trip to Belgium and the Netherlands – beautiful country with no shortage of sights to see, beer to drink and waffles to gorge on. Neither of us wanted to deal with the burden of an outrageous cellular bill at the end of the trip so we had to get creative.
Firstly, you have to enumerate what challenges you may encounter while abroad if you have no cellular data:
- Where will you stay?
- How will you get there?
- How will you get to the places you wish to visit?
- Do you know the native language? Do the people of that place speak yours?
- How will you reach out to loved ones?
I’m going to go through a few of these and offer solutions to each dilemma.
WHERE WILL YOU STAY?
Before ever leaving home, you need to plan which hotel or AirBnB you wish to stay at. If you have some sights or activities in mind that you wish to do, find a spot closest to the middle or very close to all the places that you wish to visit, depending on how urban or rural it is.
If you have a Google account, “Google My Maps” is a handy tool for visualizing this.
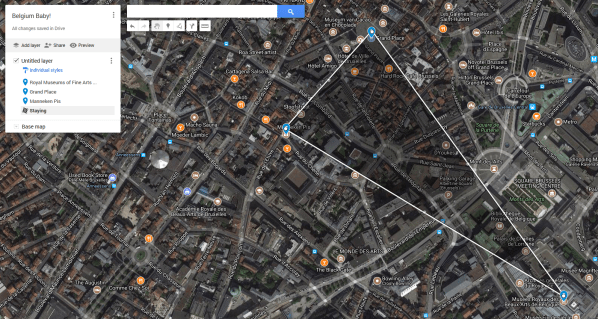
You can triangulate your stops and scroll into the middle to find hotels in the desired area within your price range.
Figure out the distance from your hotel to your destinations beforehand to get perspective on how long it would take to walk, Uber, train, or bike to the places you wish to visit.
Make certain that your hotel offers free WiFi! This is very important. Consider this free WiFi your “diving board” for the rest of your trip.
HOW WILL YOU GET THERE?
Are you flying in? Driving? Traveling by train? This may be easier for you than what we bumped into.
We flew into Brussels and decided not to rent a car, as we are quite unfamiliar with traffic laws in Belgium (or Europe in general). We decided to take a taxi to our hotel, but there are always cheaper alternatives to get you where you need to be.
When departing from your airport or station, you can use the WiFi offered there to get an Uber (iPhone / Android) or Lyft (iPhone / Android) to get you where you need to be. Taxis can be just as good, but the rates tend to be slightly higher.
HOW WILL YOU GET AROUND?
And I don’t mean that in the Tinder way. How will you reach the places you wish to visit?
If the places you want to go are close enough to your hotel, as it was for us, consider walking if the area is safe.
Google Maps (iPhone / Android) offers the ability to download a map of the area you are in and use it offline, but this only applies to driving maps. Not walking or biking. Bummer, right?
W-WRONG!
Maps.me (iPhone / Android) is a great alternative to Google Maps’ offline feature. It includes the ability to have walking maps offline and is quite reliable.
Simply install the app (while on WiFi of course), launch the app and it will start prompting you as to whether or not you want to download offline maps for that region. Yes please!
DO YOU KNOW THE NATIVE LANGUAGE?
My girlfriend and I are unwashed heathens that only speak English. Luckily for us, the Dutch are taught English in school as a secondary language and they typically speak it very well.
The story could be very different for you if you are going to a place that does not speak your native tongue as a primary or secondary language.
Reading signs, understanding television and listening to radio announcements became much easier for us when we employed the use of Google Translate (iPhone / Android).
Download languages to be available offline:

After doing so, you can now listen to speech in real-time and translate it, or even cooler, use the camera function and translate on the fly! This was an invaluable tool for us.
HOW WILL YOU REACH OUT?
Calling overseas is very expensive. If you are an iPhone user and the person you wish to communicate with is as well, you could easily use iMessage features to communicate over WiFi.
Android users don’t have a common internet messaging feature built-in with the OS, but you can arrange for loved ones to install Google Duo (iPhone / Android) or Google Allo (iPhone / Android) before you leave.
Even easier, Facebook Messenger (iPhone / Android) allows you to communicate over WiFi via text, video or voice. Everyone has Facebook, right?
An alternative that I found very useful for calling hotels to confirm bookings as well as calling family members with dumb phones (yup, people still have them!) is WePhone (iPhone / Android).
Simply purchase credits inside of the app itself and you’re ready to make calls over WiFi to anywhere in the world!
ADDITIONAL HINTS
- Keep an eye out for open WiFi networks at Cafes, hotels, tearooms and major stores. You can typically find an open network quickly in larger cities.
- Some open networks may require you to sign in – always try the obvious first. I authenticated to a captive portal by just putting in the name of the restaurant!
- Reserve power-bricks for charging on the go can be a must for those who will be heavily using a GPS-based app such as Maps.Me – keep one handy!
- Make sure you have a power outlet adapter for the country you are going to. You’ll regret it if not.
So that concludes this brief guide to survival without cellular. Hope it comes in handy for you on your next holiday. Cheers and good luck!
– b3b0🐧💻🔑
Equifax – the hack that could (and should) change it all.

At the time of this posting, there hasn’t been a statement on the specific nature of the hack – no information on the attack vector or even how many people have truly been affected. I will not concentrate on those juicy details.
Instead, let’s talk about what this hack means for us in the InfoSec field and what it means for those we protect.
I remember the Target hacks of 2013. I was just cutting my teeth as a network engineer studying to get my security certifications. This hack could not have happened at a more coincidental time for me.
Though the hack wasn’t incredibly sophisticated, it was incredibly effective. Malware was installed on a secure payment processing system, credentials were compromised via an insecure third-party HVAC vendor. The malware likely entered a worm-like phase and delegated itself to payment terminals across Target’s 1700+ stores. It was able to pull customer credit card numbers out of RAM before the CPNI was encrypted and sent across the wires. This data was stored on a Target server that had become commandeered by the hackers. It was a considerable amount of time before the security guys within the organization were aware of the attack, and even longer before the details of the hack went public. The hack potentially hit 70 million customers.
Arby’s had been hit by a similar hack in early 2017. Malware had spread to point-of-sale systems across America and 350,000 accounts potentially had been compromised – a mere 0.5% of the amount of people effected by the Target hack a few years before. Arby’s had their information together and was ready to inform the public in about three weeks.
Fast-forward to September 2017. The Equifax hack hits the news like a sack of bricks. An estimate of 143 million Americans have the most confidential of their data, protected by one of the three behemoths of credit reporting, compromised by hackers.
This should be absolutely appalling to anyone – inside or outside of the field of Information Security.
To add insult to injury, Equifax sets up a tool to check if you had been effected by the hack while simultaneously waiving your right to sue them for negligence.
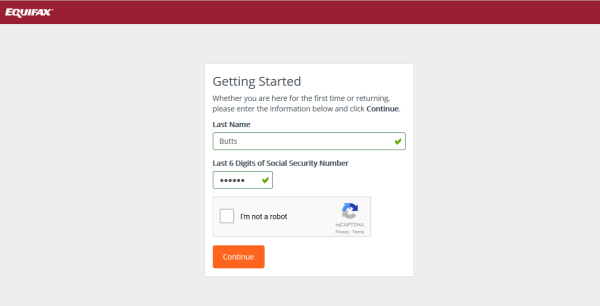
It doesn’t end there folks! Not long after, it came to light that the tool was pretty bogus, returning random results on whether or not your confidential information had been compromised.
Let’s outline this madness.
- Equifax gets hacked.
- 143 million people compromised.
- Equifax creates a tool to check if your information was lost.
- Using said tool waives your right to a class-action lawsuit against them.
- The tool turns out to spit out garbage results, a farce to buy more time and give a false sense of security.
There are too many failures to count here. Negligence, deception, and world-class ass-covering.
I won’t take time to point fingers or accuse anyone on that corporate ladder at ol’ Equifax. But it seems that they did not have the best talent, the best alerting software, or even the best tactics to undo the damage they let happen. The facts stand – this hack has the potential to be the most damaging ever. Your information may already be on the black market and in use if you haven’t frozen your credit through all three credit reporting agencies.
Why haven’t corporations learned from mistakes of the other giants? Why is security still considered a secondary thought in our ever-connected world? Why is more money spent on the graphic design of our application and software infrastructure than securing it? That goes from the developer to the administrators keeping the systems safe.
We live in the age of information. The pirates of our era can reach into your home from across the world (or from inside the same open WiFi SSID at your local coffee shop) and take your data, which represents the real YOU, and steer your ship into the ground.
Corporations cannot think of these hacks as a cost of doing business. We citizens cannot let those whom we trust with our most pertinent and confidential data get off the hook for this as we have in the past. Many companies have done the right thing and tried as best they can to repay the damage they let fall upon their customers.
- Citizens: don’t let Equifax off the hook.
- Corporations: be responsible and hire the best minds that you can.
- InfoSec Pros: keep getting better. The nature of our work never stops changing.
I could keep ranting, but will not. I have a Blue Apron to make and wine to drink. After dinner, I will do more research to try and understand how I can be better. If I do not, I could one day be a cog in the machine that allows millions of people to be at risk.
💘b3b0
Wazuh: Testing your rules and alerting with Python 2.7

This will VERY be similar to my previous post.
So you wanna make sure that your critical HIDS alerts are being monitored? Let’s get crackin’.
Wazuh is a fork of the OSSEC-HIDS project. It is a very dynamic piece of software to add to your network-intelligence-gathering toolbelt. It installs on freaking everything.
To start, make certain that your email settings are valid (on your agent manager/server) in /var/ossec/etc/ossec.conf. Including your global settings and alerts settings.
I set my email alert threshold to 7 for this excercise.
Now let’s nano or vi our local rules at /var/ossec/etc/rules/local_rules.xml.
Here’s my sample rule:
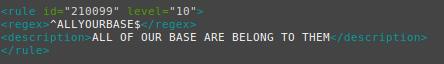
Restart your Wazuh agent manager / server with:
# /var/ossec/bin/ossec-control restart
Time to get scripting!
Make sure you have python 2.7.
$ sudo apt-get install python2.7
$ sudo apt-get install python-pip
Here’s the actual script:
import time
import sys
import os
def wazuh():
os.system('echo "ALLYOURBASE" >> /var/log/auth.log')
print("IT HAS BEEN DONE")
wazuh()
Save the script as a .py file and save it on a device that has the Wazuh agent (client) installed.
This excercise is centered around testing a Linux agent manager (server) with a Ubuntu agent client, so make adjustments to your process if you are using Windows or OSX.
Wazuh monitors /var/log/auth.log by default in Ubuntu, so that is why I chose said file for this example.
As you can see from the script, we are simply echoing “ALLYOURBASE” into this file. The rule we have created an local_rules.xml has a regex match statment, looking for that exact string of text.
Now let’s run the script:
$ sudo python2 /home/bebo/Code/python2/allyourbase.py
If there are no errors, your terminal should return “IT HAS BEEN DONE”.
Check out your alert in real-time in /var/ossec/logs/alerts/alerts.log:
# tail -f /var/ossec/logs/alerts/alerts.log
You should see your alert tick right through!
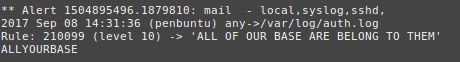
If your email settings are valid, you should also receive an email alert.

Holy crap! Things are working!
You can view source for this snippet at:
https://github.com/b3b0/allyourbase/blob/master/allyourbase.py
Security Onion: Testing your rules with Python 2.7 & the SCAPY library

There are times that we need to make sure that we have granular control over how well our IDS is alerting. Sometimes you may as well put yourself into a tizzy asking, “Am I able to see what I REALLY need to?”
A way to accomplish this with Security Onion is to create custom rules in /etc/nsm/rules/local.rules
My rule will be simple.
alert tcp any any -> $HOME_NET 999 (msg:"WE'VE BEEN RICK ROLLED"; content:"NEVERGONNAGIVEYOUUP"; flow:to_server; classtype:diagnostic; sid:12000006; rev:1)
If you have already defined your home network, then this is pretty straight forward. I used a sid that I was certain not to fire another rule message name.
In /etc/nsm/securityonion/sguild.email, configure your sguild alerts to alert on this sid:
# EMAIL_ENABLE_SIDS: A list of snort IDS (sids) that you want to enable, but are NOT
# included in EMAIL_CLASSES. NOTE: This overrides EMAIL_DISABLE_SIDS.
# 0=none
set EMAIL_ENABLE_SIDS "12000006"
Perform:
# nsm_server_ps-restart && rule-update
Now your Security Onion box is ready to alert you.
Let’s make a script now!
Make sure you have python 2.7 and python-pip:
$ sudo apt-get install python2.7
$ sudo apt-get install python-pip
Then let’s get the scapy library for Python:
$ sudo pip install scapy
The actual script is very simple:
import time
import sys
import os
from scapy.all import *
list = open("dests.txt").readlines()
#####################
#if you want to specify many destinations to test multiple sensors, use this list statement.
#####################
def ids():
for x in list:
packet = IP(dst=x,src="YOUR IP")/TCP(dport=999,sport=1234)/"NEVERGONNAGIVEYOUUP"
send(packet)
print("A PACKET HAS BEEN SENT TO " + x)
time.sleep(2)
ids()
Make sure to put in a source IP that is routable on the network from the location in which you launch this script.
Finally, save this script as a .py file and run it. Like so:
$ sudo python2 /home/bebo/Code/python2/rickroll.py
If you don’t get any error messages, then you can check SGUIL and your email for alerts.

Success!
You can view source for this snippet at:




